Recent searches
Search options
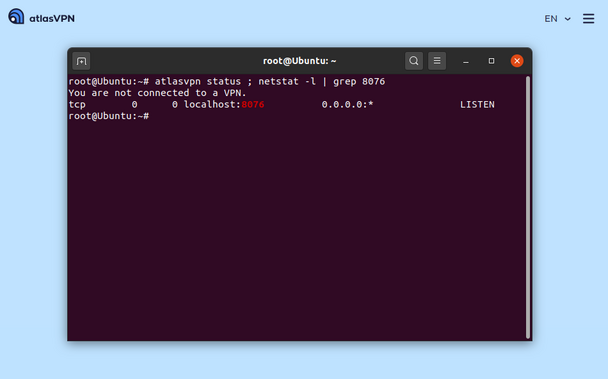
Find of the day - someone dropped an AtlasVPN #0day on Reddit. The AtlasVPN daemon on Linux runs an HTTP server to accept CLI commands, it binds to 127.0.0.1:8076 by default.
What's hilarious is that it accepts commands without ANY authentication - so if you open a malicious webpage, that webpage can fire a POST to 127.0.0.1:8076/connection/stop and instantly disconnect your VPN.
Utter garbage.
Source: https://www.reddit.com/r/cybersecurity/comments/167f16e/atlasvpn_linux_client_103_remote_disconnect/
Proof below - used AtlasVPN's latest Linux client, version 1.0.3.
@tweedge the fuck??? What is that even used for?
@benjistokman Looks like the VPN daemon is always running, even when it's not connected, and the VPN takes commands from that HTTP server. Here's it that same server listening when the VPN is not connected: